14) which of the following are breach prevention best practices
Which of the following are breach prevention best practices. Access only the minimum amount of PHIpersonally identifiable information PII necessary.

10 Crucial Steps For Protecting Your Company From Cyber Attacks
Promptly retrieve documents containing PHIPHI from the printer D.

. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above. A single technology cannot provide complete protection. See Page 1.
The following best practices may help. Implementing encryption standards and backup policies to decrease risks and make sure that software is up-to-date and patched regularly is vital to limiting the vulnerability of networks. All of the above.
Perform regular vulnerability assessments. In a hyper-connected business world organizational leaders understand that data breaches are a fact of life. Which of the following are breach prevention best practices.
You Need to Be Aware of. Logoff or lock your workstation when it is unattended C. Which of the following are true statements about limited data sets.
Pc Emergency Readiness Staff. Vulnerability assessment is the process intended to identify classify and prioritize security threats and determine the risks. However providing we can answer the following questions we will be in a much better position to prevent data breaches as well as avoid the lawsuits and potentially large fines.
Attracting new customers or regaining the loyalty of existing customers following a successful and widely publicized breach is very difficult task. Identity sensitive data collected stored transmitted or processes. Data Breach Prevention Best Practices Ensure youre using Encryption.
According to NIST organizations should use encryption for all stored. Data Loss Prevention DLP solutions can assist companies in avoiding data breaches by applying. However these 30 best practices for preventing a data breach can reduce the risk and respond to an attack more effectively.
Public Health Nigeria Public Health Nigeria an Interdisciplinary public health movement focused on health education advancing fair public health policies promoting fitness healthy diets responsible behavior community health and general wellbeing. PCs cell phones PDAs and the network says Pappas. Data Breach Prevention Tools.
Encryption protects data from being stolen or intercepted and without it hackers have a much easier time stealing information. 2 Which of the following are breach prevention best practices. A breach as defined by the DoD is broader than a HIPAA.
In which of the following circumstances must an individual be given the opportunity to agree or object to the use and disclosure of their PHI. Promptly retrieve documents. Which of the following are breach prevention best practices.
Developing policies and procedures and implementing best practices will at the very least diminish the potential. A- True right B- False 18 When should a breach be reported to the US. Now with the GDPR in full effect we will likely see these costs increase.
Access only the minimum amount of PHIpersonally identifiable information PII necessary B. Addresses three types of safeguards - administrative technical and physical. The best way to avoid being a victim of a breach is to prioritize data security.
List of 10 Breach Prevention Best Practices. PCs cell phones PDAs and the network says Pappas. Select the best answer.
A- Inside 1 hours of discovery right B- Inside 24 hours of discovery. Make sure your organization is using encryption to protect sensitive data. Which of the following are breach prevention best practices.
All of the above. Before you can prevent a data breach. If an individual believes that a DoD covered entity CE is not complying with HIPAA.
All of the above. What of the following are categories for punishing violations of federal health care laws. Furthermore many countries have data breach notification laws requiring both private and public entities to notify individuals of breaches involving personal information.
He recommends campuses have firewalls. 17 A breach as outlined by the DoD is broader than a HIPAA breach or breach outlined by HHS. In the United States the average total cost of a data breach stands at 819 million more than twice the global average.
Which of the following are breach prevention best practices. They need to be secure at the host eg. Which of the following are breach prevention best practices.
Logoff or lock your workstation when it is unattended.

How To Secure Reactjs App Reactjs Security Best Practices To Follow

Develop A Security Operations Strategy Info Tech Research Group

Orca Security Launches Industry S First Cloud Risk Encyclopedia To Provide Ongoing Education For Cloud Security Best Practices Business Wire

Phishing Awareness Best Practices For Email Testing Currentware
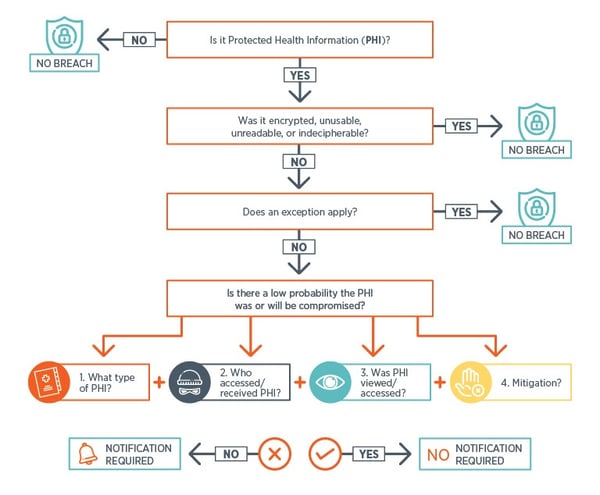
Preventing Hipaa Data Breaches Case Studies And Best Practices
7 Key Coverage Elements Of Cyber Liability Insurance

Phishing Awareness Best Practices For Email Testing Currentware

How To Prevent A Breach Attack Crashtest Security

The Top Six Cybersecurity Risks Facing Your Small Business
Pharmaceutical Data Integrity Issues Challenges And Proposed Solutions For Manufacturers And Inspectors Gabi Journal

How To Secure Reactjs App Reactjs Security Best Practices To Follow

Data Loss Vs Data Leaks What S The Difference Upguard

Data Breaches And Cybersecurity Incidents The Legal Guide To Preparedness And Response Osgoodepd
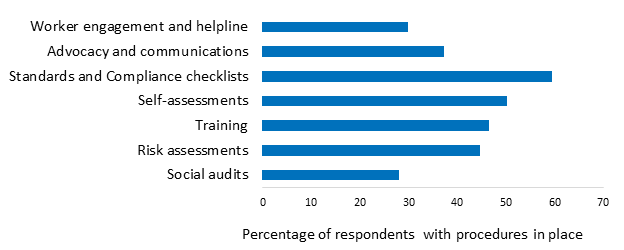
What We Heard Report Revisions To The Code Of Conduct For Procurement Buying And Selling Pspc

What Is Digital Identity Why Does It Matter Hashed Out By The Ssl Store

The Definitive Cyber Security Guide For Small To Medium Businesses

Email Security A Guide To Advanced Threat Protection Ironscales

